Introduction
Transaction isolation levels are critical for maintaining data consistency in relational databases. This article dissects PostgreSQL’s implementation of ACID-compliant isolation levels through source code analysis, comparing behaviors across Read Committed, Repeatable Read, and Serializable modes.
Isolation Level Overview
PostgreSQL supports three of the four SQL-standard isolation levels:
- Read Committed: Default mode; transactions see only committed data.
- Repeatable Read: Guarantees consistent reads within a transaction.
- Serializable: Highest isolation; prevents all concurrency anomalies.
Implementation Details
1. Read Committed Isolation
Mechanism:
- Utilizes MVCC (Multi-Version Concurrency Control) to generate a new snapshot for each query.
- Ensures dirty reads are impossible but may allow non-repeatable reads.
Source Code Insight:
-- Query snapshot generation during transaction start
BEGIN TRANSACTION ISOLATION LEVEL READ COMMITTED;
SELECT xmin, xmax, * FROM test_table WHERE id = 1;
2. Repeatable Read Isolation
Mechanism:
- Uses a fixed snapshot for the entire transaction.
- Blocks phantom reads by tracking active transactions.
Key Code Snippet:
/* In src/backend/utils/time/snapmgr.c */
if (IsolationUsesXactSnapshot()) {
/* Reuse existing snapshot for repeatable reads */
CurrentSnapshot = GetTransactionSnapshot();
}
3. Serializable Isolation
Mechanism:
- Employs SSI (Serializable Snapshot Isolation) to detect conflicts.
- Rolls back transactions to prevent serialization anomalies.
Concurrency Control:
-- Example of serialization failure
BEGIN TRANSACTION ISOLATION LEVEL SERIALIZABLE;
UPDATE accounts SET balance = balance - 100 WHERE id = 1;
-- May fail if another transaction modified the same row
COMMIT;
Performance vs. Consistency Tradeoffs
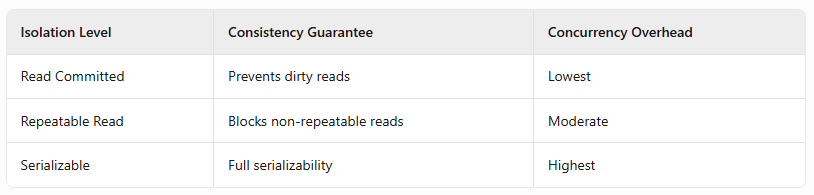
Optimization Tips:
- Prefer Read Committed for most OLTP workloads.
- Use Serializable only when strict consistency is mandatory.
Conclusion
PostgreSQL’s isolation levels leverage MVCC and advanced locking mechanisms to balance performance and consistency. By understanding their source-level implementations—especially snapshot management and conflict detection—developers can optimize transactional workflows for their specific use cases.
%20(2048%20x%201000%20%E5%83%8F%E7%B4%A0)%20(3).png)

%20(2048%20x%201000%20%E5%83%8F%E7%B4%A0)%20(2).png)
